DoH, or Don't?
Carsten Strotmann, dnsworkshop.de
CCCamp 2019
Created: 2019-08-21 Wed 08:37
Agenda
- DNS-Privacy
- DoH/DoT/DoQ
- The Dilemma
- Summary
About me?
Carsten Strotmann
DNS(SEC)/DANE/DHCP/IPv6 trainer and supporter
RIPE/IETF
Privacy in DNS?
- in recent years, the IETF has expanded the DNS protocol with
privacy features
- DNS-over-TLS (transport encryption between DNS client and DNS resolver)
- DNS-over-HTTPS (transport encryption between DNS client and DNS resolver)
- QNAME Minimization (less metadata in DNS)
- EDNS-Padding (hiding of DNS data in encrypted connections)
The need for more DNS privacy
- a study presented at IETF 105 during the Applied Networking Research
Workshop in July 2019 found that
- 8.5 % of networks (AS) intercept DNS queries (27.9% in China)
- (today) most queries are answered un-altered
- but the situation might change, intercept server might change DNS answers
encrypted transport for DNS
- Terminology
Do53= DNS-over-Port53 - classic DNS (UDP/TCP port 53)DoT= DNS-over-TLS - TLS as the transport for DNSDoH= DNS-over-HTTPS - HTTPS as the transport for DNSDoQ= DNS-over-QUIC - QUIC as the transport for DNSDoC= DNS-over-Cloud - DNS resolution via cloud services (Google, Q9, Cloudflare …)
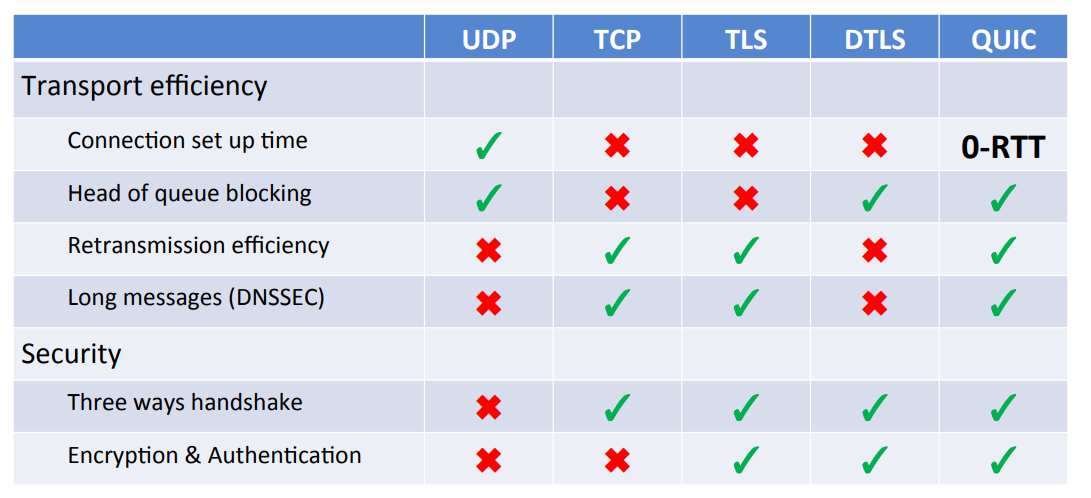
Performance of DoT/DoH (1/2)
- with TLS 1.3 performance of DoT/DoH is quite good
- with established connections, performance can be similar to DNS-over-UDP due to
- Pipelining
- TCP fast open
- 0-RTT resume
- on connections with packet loss, DoT/DoH can be faster and more reliable than Do53!
- not all implementations are fully optimized
Performance of DoT/DoH (2/2)
- Mozilla found that in lossy networks DoH can be faster and more reliable than Do53
- The study "Analyzing the Costs (and Benefits) of DNS, DoT, and DoH for the Modern Web" presented at Applied Networking Research Workshop July 2019 confirms that finding
DoT - DNS-over-TLS
- RFC 7858 "Specification for DNS over Transport Layer Security (TLS)"
- DNS wireformat over TLS over TCP
- Port 853 (TCP)
- Encryption and Authentication (Internet PKI or via DANE)
DNS-over-TLS (1/3)
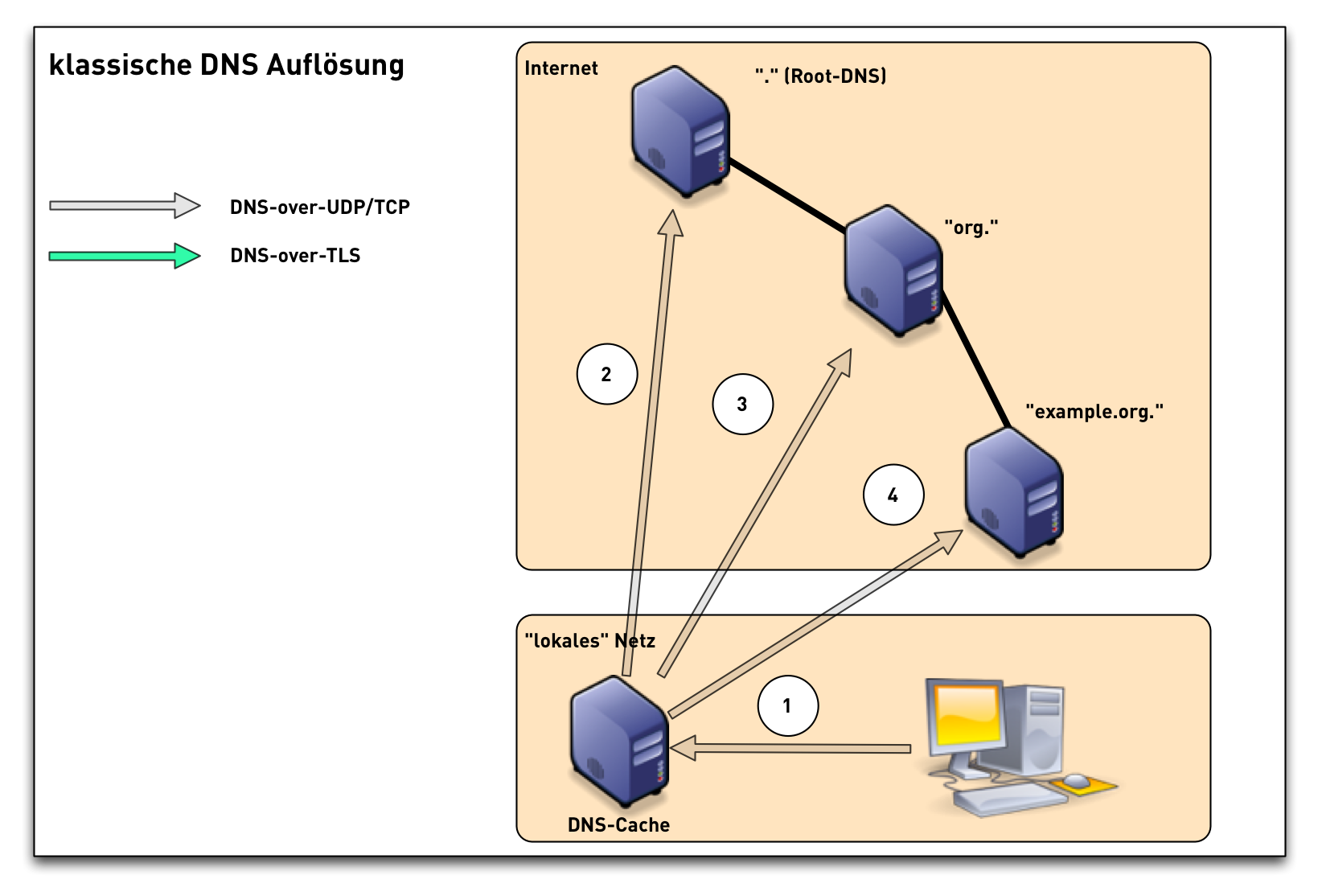
DNS-over-TLS (2/3)
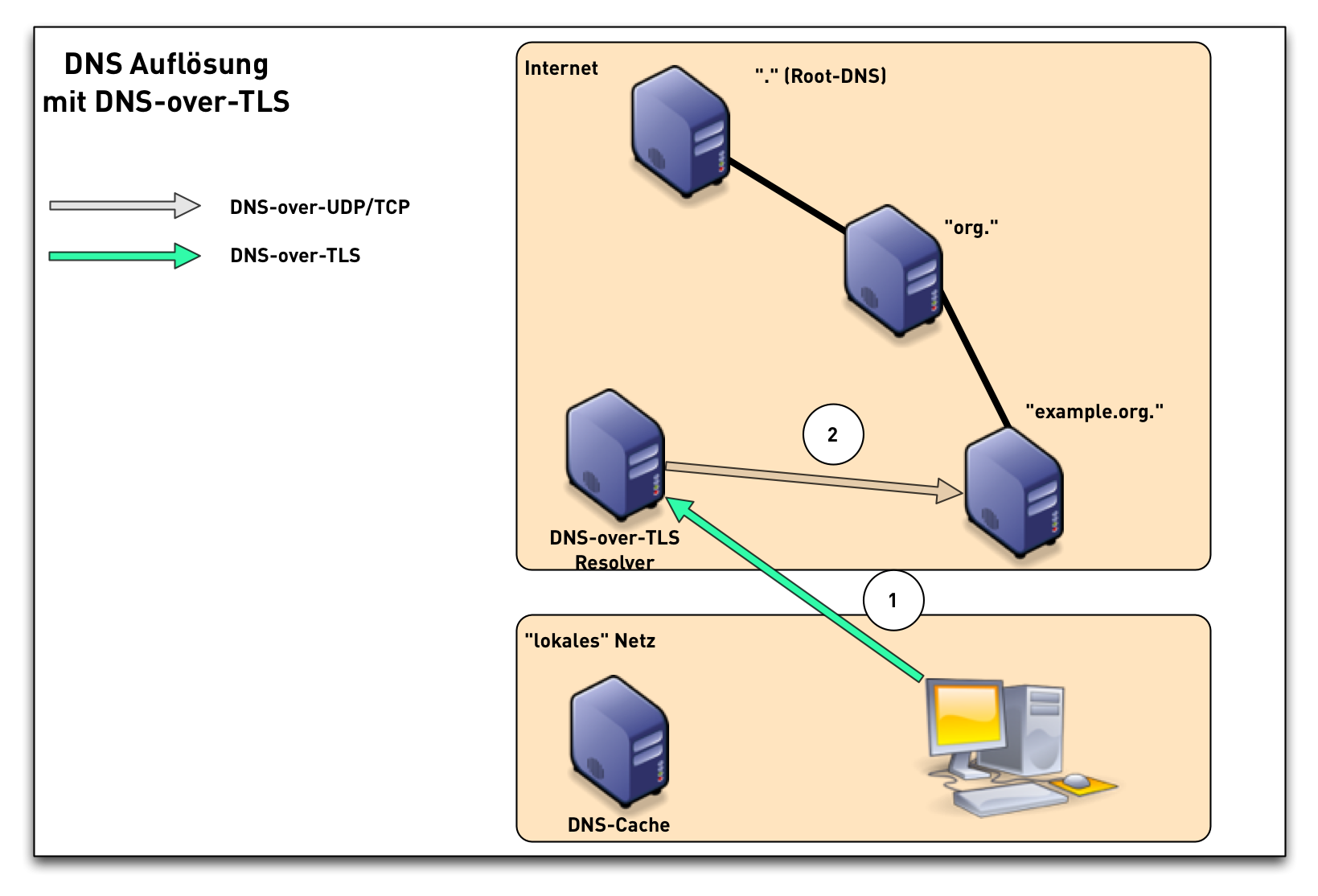
DNS-over-TLS (3/3)
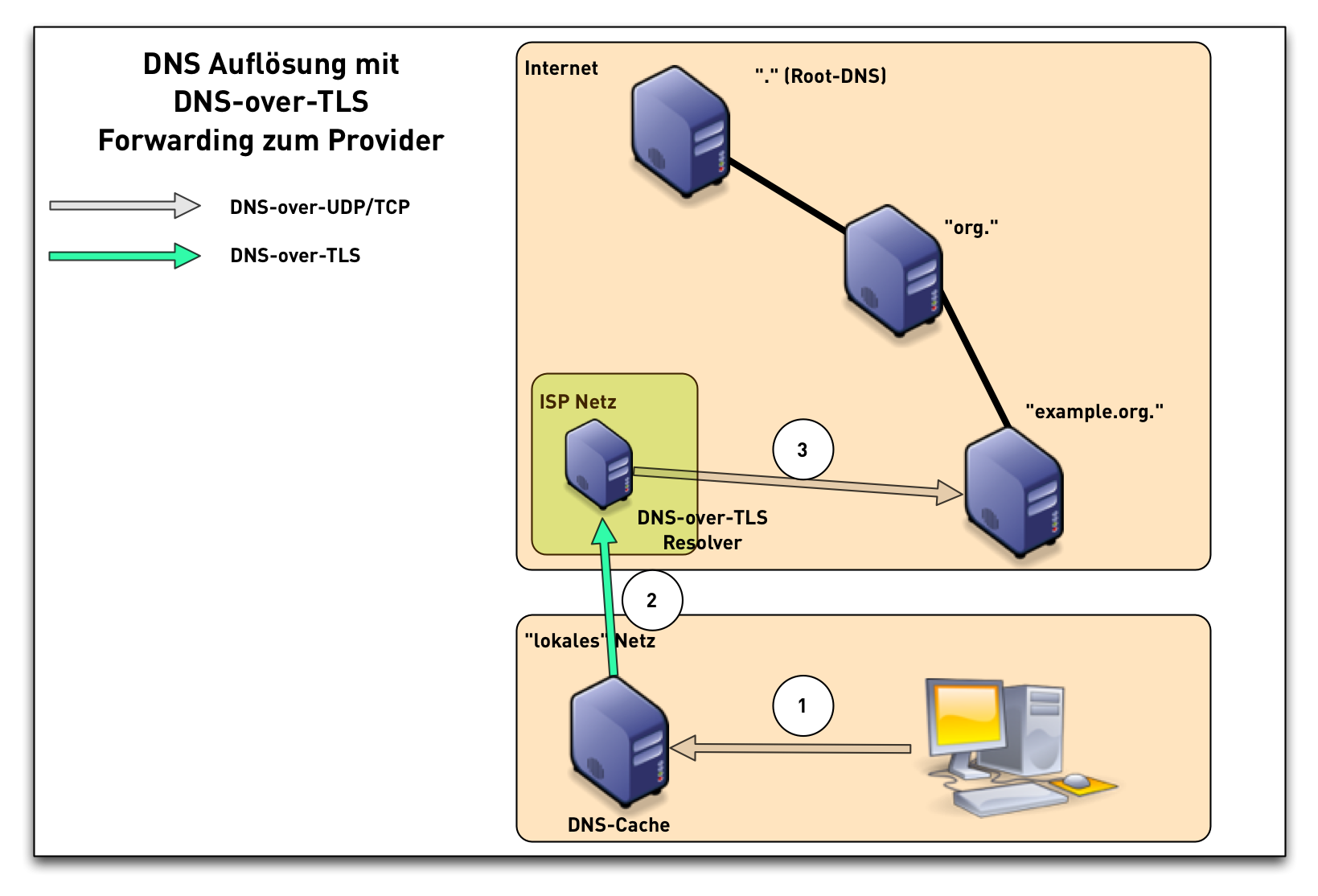
DNS-over-TLS modes
- DNS-over-TLS can be operated in two modes
- opportunistic - try TLS authentication, but still use server in case authentication fails
- strict - only use server if there are no errors in the TLS connection
DNS-over-TLS operators
DoH - DNS over HTTP(S)
- RFC 8484 DNS Queries over HTTPS (DoH) (P. Hoffman, ICANN and P. McManus, Mozilla) https://tools.ietf.org/html/rfc8484
- DNS HTTP-Format over HTTPS over TCP, Port 443 (HTTP/2)
- URL: https://server/dns-query{?dns}"
- Encryption, Authentication and Cloaking
DoH - DNS-over-HTTPS
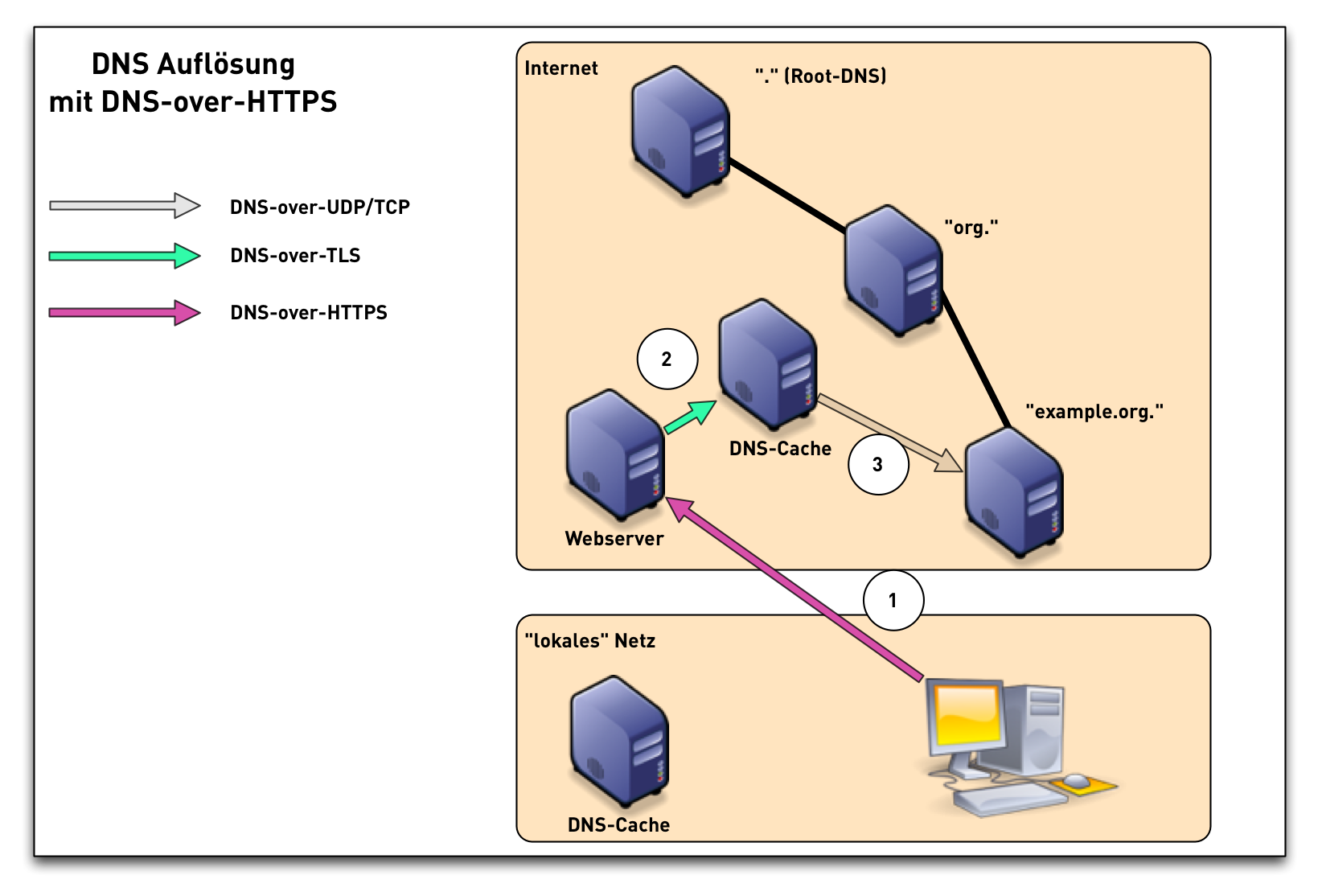
DoH timeline
- IETF 100 - November 2017 - DNS over HTTP(S) (DoH) workinggroup started: https://datatracker.ietf.org/wg/doh/about/
- IETF 101 - March 2018 - work on DNS Queries over HTTPS finished, start of working group last call (WGLC) in April 2018
- October 2018 - RFC 8484 published
DNS-over-HTTPS and IDS/Network-filter
Quote from RFC 8484:
Operational Considerations […] Filtering or inspection systems that rely on unsecured transport of DNS will not function in a DNS over HTTPS environment due to the confidentiality and integrity protection provided by TLS.
DoH in Firefox (1/3)
- Firefox 61+ (manual switch)
- Firefox TRR Konfigurations Optionen
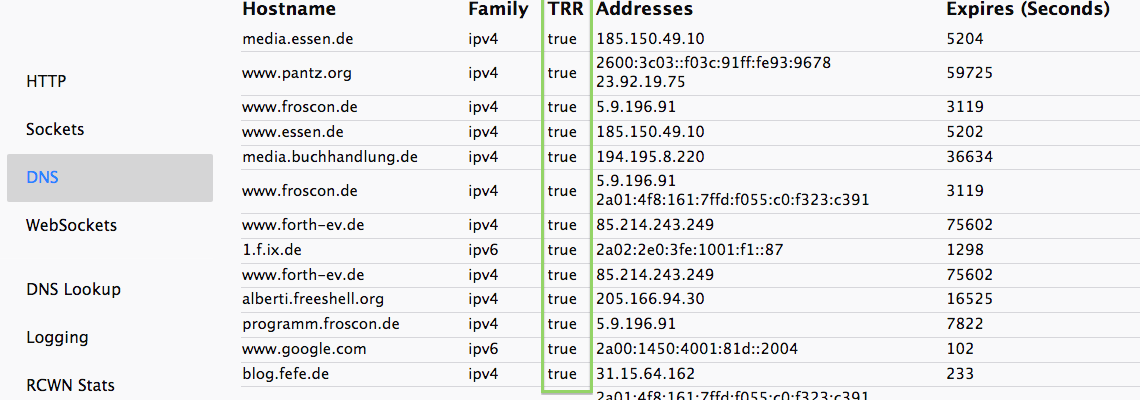
DoH in Firefox (2/3)
- Firefox Quantum (Screenshot FF 68)
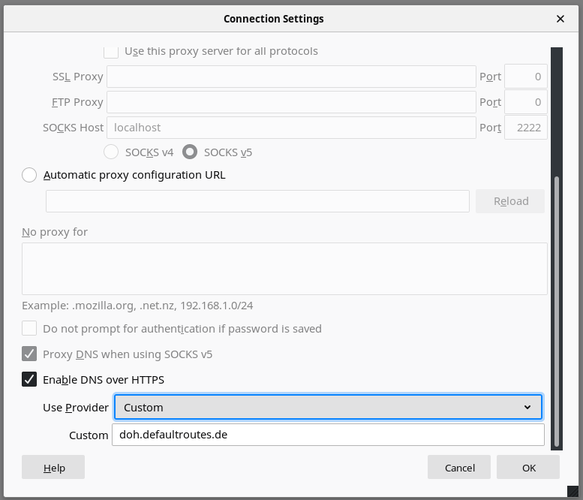
DoH in Firefox (3/3)
- Mozilla plans to enable DoH in Firefox by default in the future. No date announced.
- User can select among a list of certified DoH operators per "region"
- operators of DoH services can apply for privacy certification
- Mozilla Policy Requirements for DNS over HTTPs Partners: https://wiki.mozilla.org/Security/DOH-resolver-policy
DoH in Google Chrome
- currently, DoH can be enabled in Chrome via commandline switches https://judge.sh/how-to-enable-dns-over-https-on-chrome-right-now/
- a GUI configuration is coming with Chrome Version 78
- Google has no plans to enable DoH by default
DoH operators (Selection)
- Cloudflare https://cloudflare-dns.com/dns-query
- Cloudflare/Mozilla https://mozilla.cloudflare-dns.com/dns-query
- Clean Browsing https://doh.cleanbrowsing.org/doh/family-filter/
- PowerDNS https://doh.powerdns.org
- BlahDNS (de) https://doh.de.blahdns.com/dns-query
- SecureDNS https://doh.securedns.eu/dns-query
DoT vs DoH
- differences between DoT and DoH
- DoT can be easily blocked, because it is running on an dedicated port (853)
- DoH is made to look like normal HTTPS traffic, selective blocking of DoH is difficult
- DoH seems to be easier to implement, because of existing HTTPS library functions in programming languages
- DoH enables developers to do DNS name resolution on an application level, which some people think is bad
The DoH dilemma
- to reach the Internet users that are in need of privacy, DoH needs
to be enabled by default
- DoH Server selection can be seen as similar to the CA selections browsers do
- a fixed selection "per region" will (still) lead to centralization
of all DNS queries with a few DNS operators
- but that might still be the case even without DoH, some countries in Asia send > 90% of DNS queries to DoC (Google)
DoH and DoT Software - only browser?
- new DNS privacy protocols sparked a large number of new software projects
- this part of the presentation will look at
- comparison of the start of new software projects in comparison to the new standards
- number of projects for DNS-over-HTTPS vs. DNS-over-TLS
- programming languages used to implement the new protocols
The survey
- looked at 55 DoT/DoH open source software projects on Github and Gitlab
- done in May 2019 and June 2019
- only software products, no composition projects (Docker Container etc)
- full list: https://doh.defaultroutes.de/implementations.html
- see presentation at RIPE 78 and recent blog post in the APNIC blog (linked from the page above)
Languages
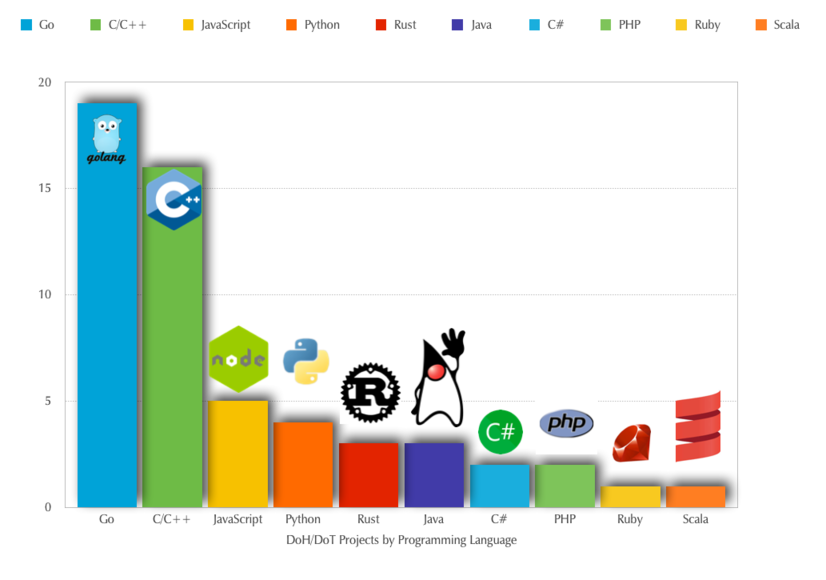
DoT vs DoH
Which protocols are implemented. Some projects implement both:
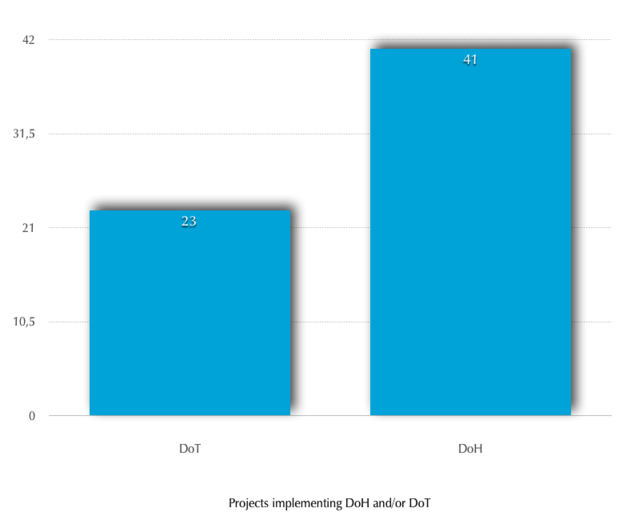
Project start
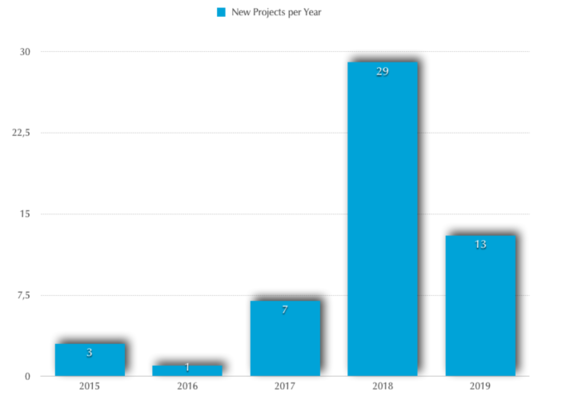
Year of the first commit, frist release or when DoH/DoT functions were implemented
Freshness
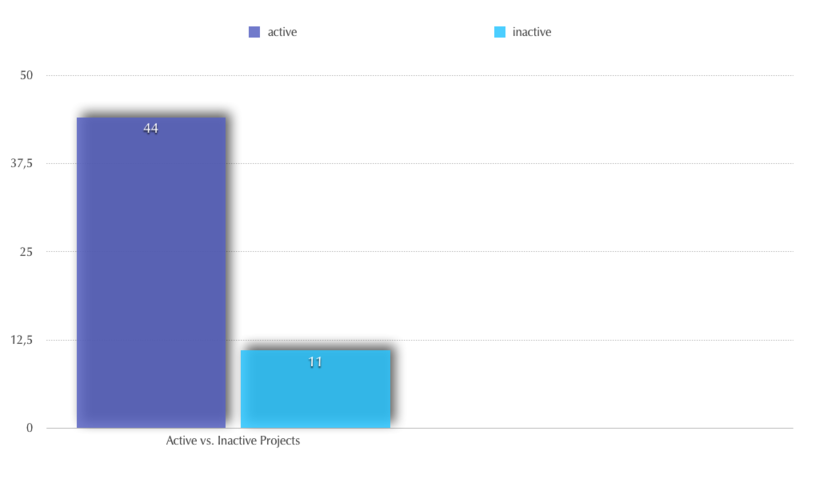
Activity in the project in the last 6 month?
Applications
- Firefox
- Chrome
- curl
- Tenta-Browser
- Bromite
System Resolver
- systemd-resolved
- unwind
- resolver module for Linux glibc
Client-Proxies
- sdns
- dnscrypt-proxy2
- veild
- stubby
- unbound
- cloudflared
- Dohnut
- dns-over-https
Server-Proxies
- rust-doh
- dnsdist
- dns-over-https
Server
- unbound
- Knot
- sdns
Whats missing in DoH/DoT software
- certificate authentication via DANE
- Wittness function - query multiple provider and compare response data
- security audits of DoH/DoT software
DNS over QUIC - the future of DNS?
- DNS over QUIC over UDP
- Specification of DNS over Dedicated QUIC Connections https://tools.ietf.org/html/draft-huitema-quic-dnsoquic
what is QUIC
- modern TCP replacement from Google, being currently standardized in the IETF
- based on UDP, implements TCP features
- implemented as part of the application, not the OS
- includes TLS 1.3
- 0-RTT
- DoQ similar to Do53 (DNS-over-UDP)
- QUIC IETF WG documents https://tools.ietf.org/wg/quic/
DNS over QUIC
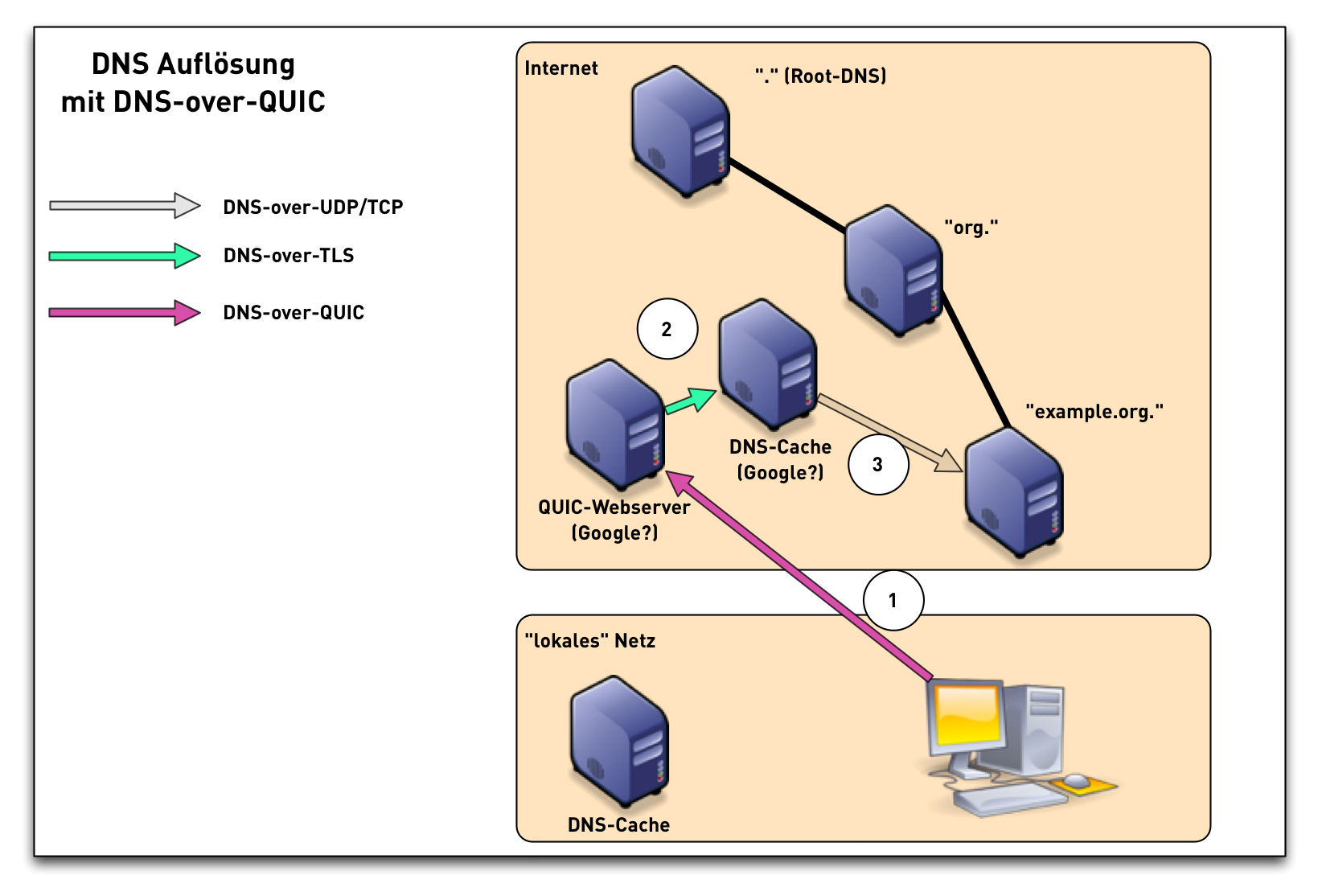
DNS over QUIC Comparision
Summary (1/2)
- the DNS protocol is evolving fast these days
- in the future, DNS communication between client and resolver will be encrypted (DNS-over-TLS, DNS-over-HTTPS, DNS-over-QUIC)
- DNS-over-HTTPS/QUIC has potential for centralization or de-centralization
Summary (2/2)
- what can be done?
- operate DoH or DoT server (responsibly)
- hack on DoH/DoT software (security audit, "witness" function)
- bring DoH/DoT into open source operating systems
- use DoH/DoT and provide feedback to the projects
- engage with the IETF
- deploy DNSSEC
Thank you
Discussion (@Digitalcourage)
Contact: cstrotm@dnsworkshop.de
Links
- Passive DNS Replication https://www.first.org/conference/2005/papers/florian-weimer-paper-1.pdf
- RFC 7858 "Specification for DNS over Transport Layer Security (TLS) https://tools.ietf.org/html/rfc7858
- DNS-over-TLS in Android 9
- DNS-over-TLS implementations https://doh.defaultroutes.de/implementations.html
- DNS-over-TLS operator (selection)
- Cloudflare/APNIC https://developers.cloudflare.com/1.1.1.1/dns-over-tls/
- Quad9 Resolver https://www.quad9.net/
- SurfNET https://dnsprivacy.org/wiki/display/DP/DNS+Privacy+Test+Servers
- Verisign https://dnsprivacy.org/wiki/display/DP/DNS+Privacy+Test+Servers
- DNS over HTTPS
- DNS-over-HTTPS RFC 8484 https://tools.ietf.org/html/rfc8484
- Google DNS-over-HTTPS Dienst https://developers.google.com/speed/public-dns/docs/dns-over-https
- OpenResolve https://www.openresolve.com/
- DinGO https://github.com/pforemski/dingo
- CoreDNS https://coredns.io/2016/11/26/dns-over-https/
- DNS-over-QUIC
- IETF Draft https://tools.ietf.org/html/draft-huitema-quic-dnsoquic
- QUIC Documents https://tools.ietf.org/wg/quic/
- Is the DNS evolving to fast?
- “The DNS Camel”, or, the rise in DNS complexity https://blog.powerdns.com/2018/03/22/the-dns-camel-or-the-rise-in-dns-complexit/
- RFC 8324 - DNS Privacy, … Time for Another Look? https://tools.ietf.org/html/rfc8324
- July 2019 ANRW Workshop (Videos and Proceedings) https://irtf.org/anrw/2019/program.html
- Who Is Answering My Queries:Understanding and Characterizing Interception of the DNS Resolution Path http://delivery.acm.org/10.1145/3350000/3341122/p15-liu.pdf
- Analyzing the Costs (and Benefits) of DNS, DoT, and DoH for the Modern Web https://irtf.org/anrw/2019/program.html