The End of DNS as we know it …
Carsten Strotmann, Men & Mice
Created: 2018-09-22 Sat 23:16
Agenda
- Privacy despite DNS - is that possible?
- DNS-over-TLS
- DNS-over-HTTPS
- DNS-over-QUIC
- QNAME-Minimization
Slides on https://doh.defaultroutes.de
Who am I?
Carsten Strotmann
menandmice.com dnsworkshop.org
DNS(SEC)/DANE/DHCP/IPv6 Trainer/Consultant
Privacy with DNS - possible?
- the IETF has expanded the good old DNS-Protocol with new security
functions in the last few years
- DNS-over-TLS (Transport encryption between DNS-Client and DNS-Server)
- DNS-over-HTTPS (Hide DNS-Requests inside Web-Communication)
- QNAME Minimization (Reduction of Metadata)
- EDNS-Padding (hiding the payload size of DNS-Data in encrypted connections)
- NSEC[3] "agressive use" - fight DDoS attacks with the help of DNSSEC
DoT - DNS-over-TLS
- RFC 7858 "Specification for DNS over Transport Layer Security (TLS)"
- DNS wireformat over TLS over TCP
- Port 853 (TCP)
- Encryption and Authentication (CA-Model or DANE)
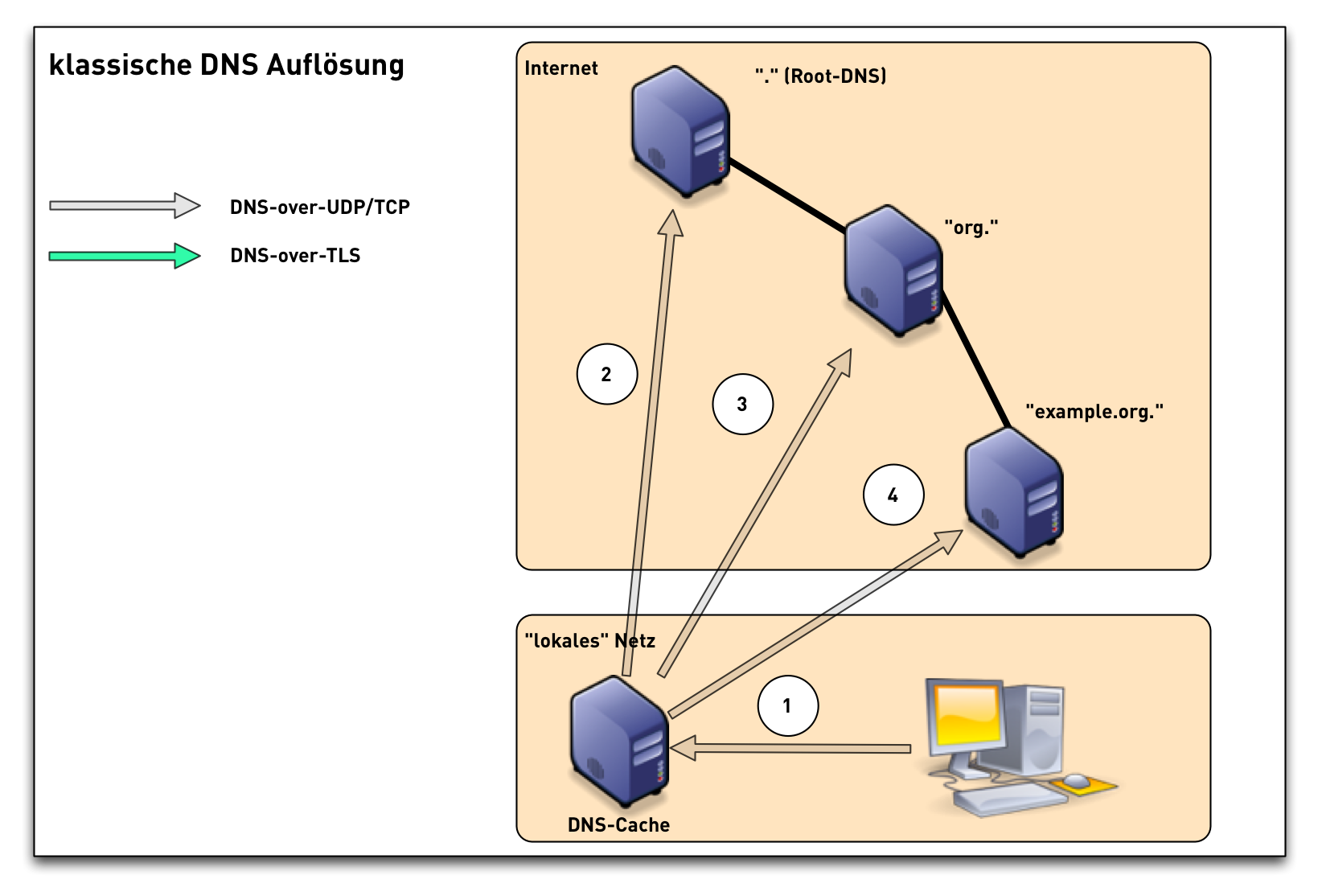
DNS-over-TLS (1/3)
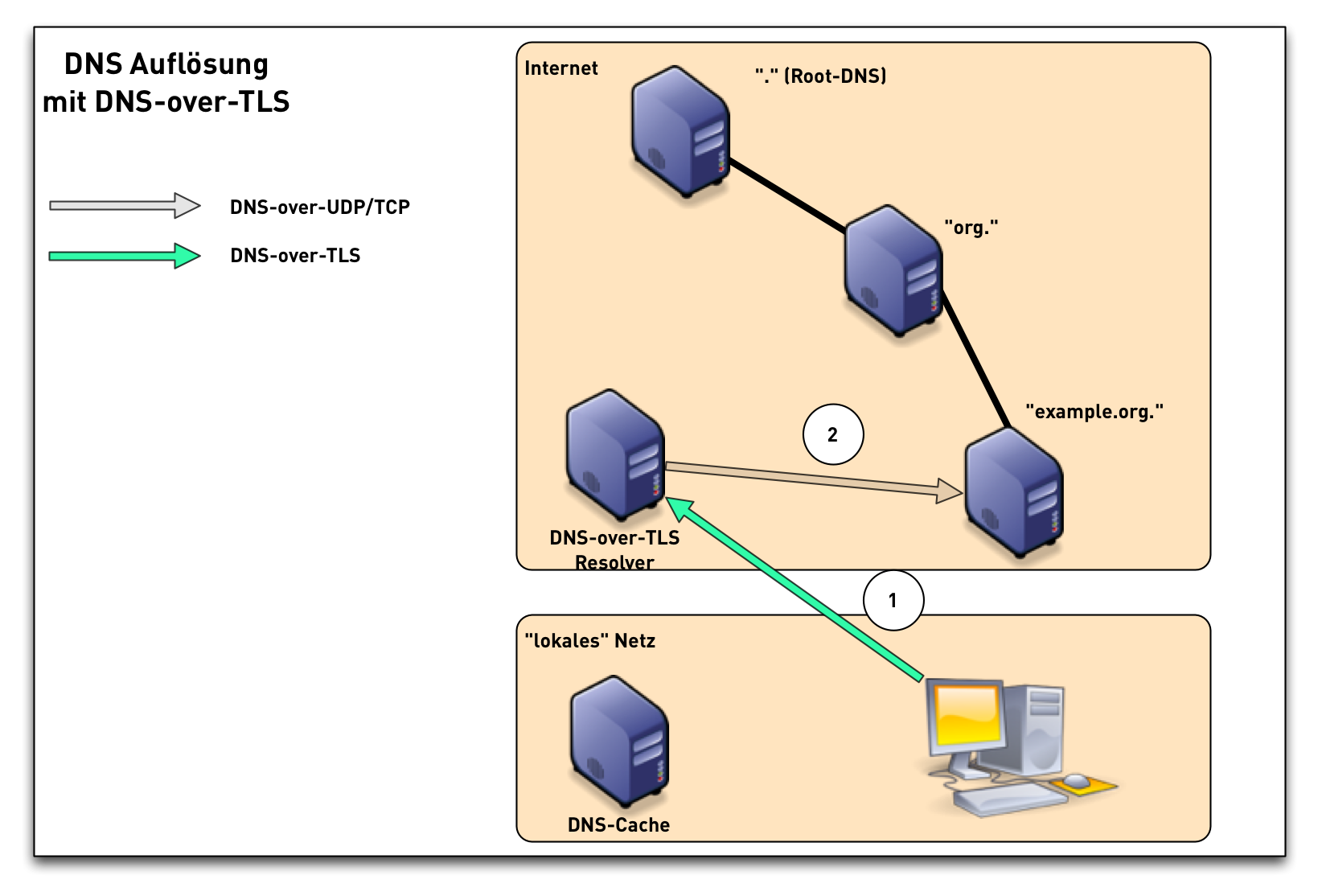
DNS-over-TLS (2/3)
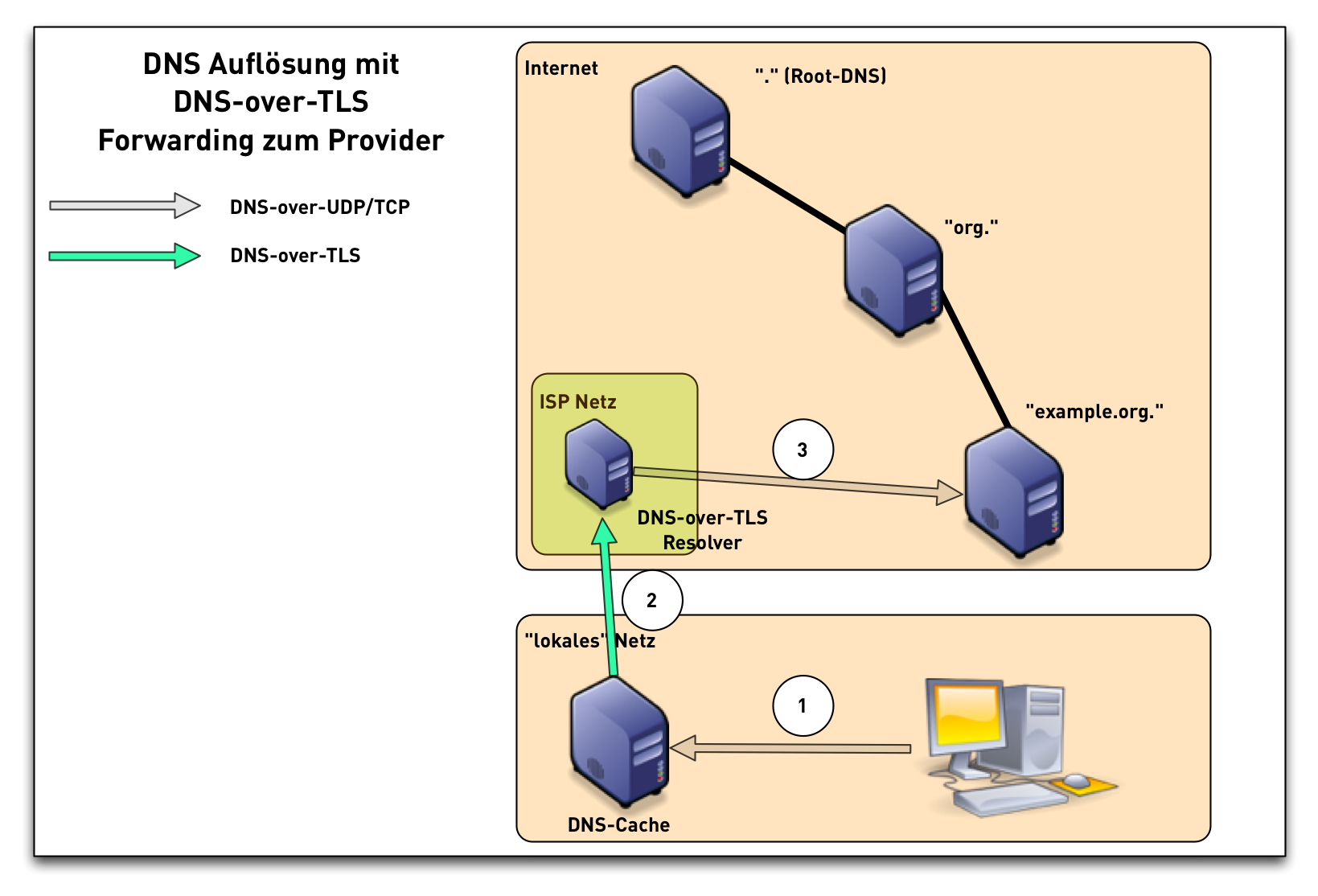
DNS-over-TLS (3/3)
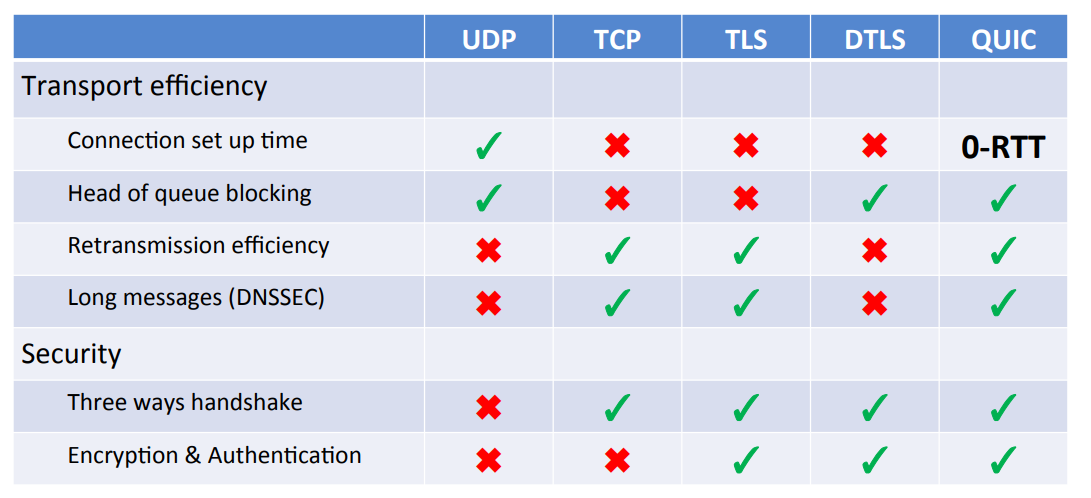
DNS-over-TLS Performance
- when using TLS 1.3, Performance/Latency of DNS-over-TLS is good
- once the connection is open, performance can be in par with
DNS-over-UDP, due to
- Pipelining
- TCP fast open
- 0-RTT resume
- unfortunaltly, most current implementations are not optimized
DNS-over-TLS modes
- DNS-over-TLS defines two usage modes
- opportunistic - try TLS, but continue without in case TLS is not available
- strict - only exchange data with the server over TLS, fail if TLS or authentication is not available
DNS-over-TLS Client Implementations
- DoT Client Implementations
- Android "Pi" (9)
- Linux systemd
- Knot-DNS / Unbound / PowerDNS dnsdist Load-Balancer
- DNS Privacy Daemon - Stubby
- jDNSProxy Simple fast and lightweight DNS proxy and cache, implementing DNS-over-TLS, DNS-over-HTTPS, and Serve-Stale
- YourFriendlyDNS
- (DNSCrypt-Proxy DNScrypt stamps for DoTLS defined)
DNS-over-TLS Server Implementations
DNS-over-TLS provider
DOH - DNS over HTTP(S)
- IETF Internet Draft DNS Queries over HTTPS (P. Hoffman, ICANN and P. McManus, Mozilla) https://tools.ietf.org/html/draft-ietf-doh-dns-over-https
- Status: Submitted to IESG for Publication
- DNS HTTP-Format over HTTPS over TCP, Port 443 (HTTP/2)
- URL (proposed): https://server/.well-known/dns-query
- encryption and authentication
- Firefox Beta-Test got negative press beginning of August 2018 based on a blog post on https://ungleich.ch
DNS-over-HTTPS
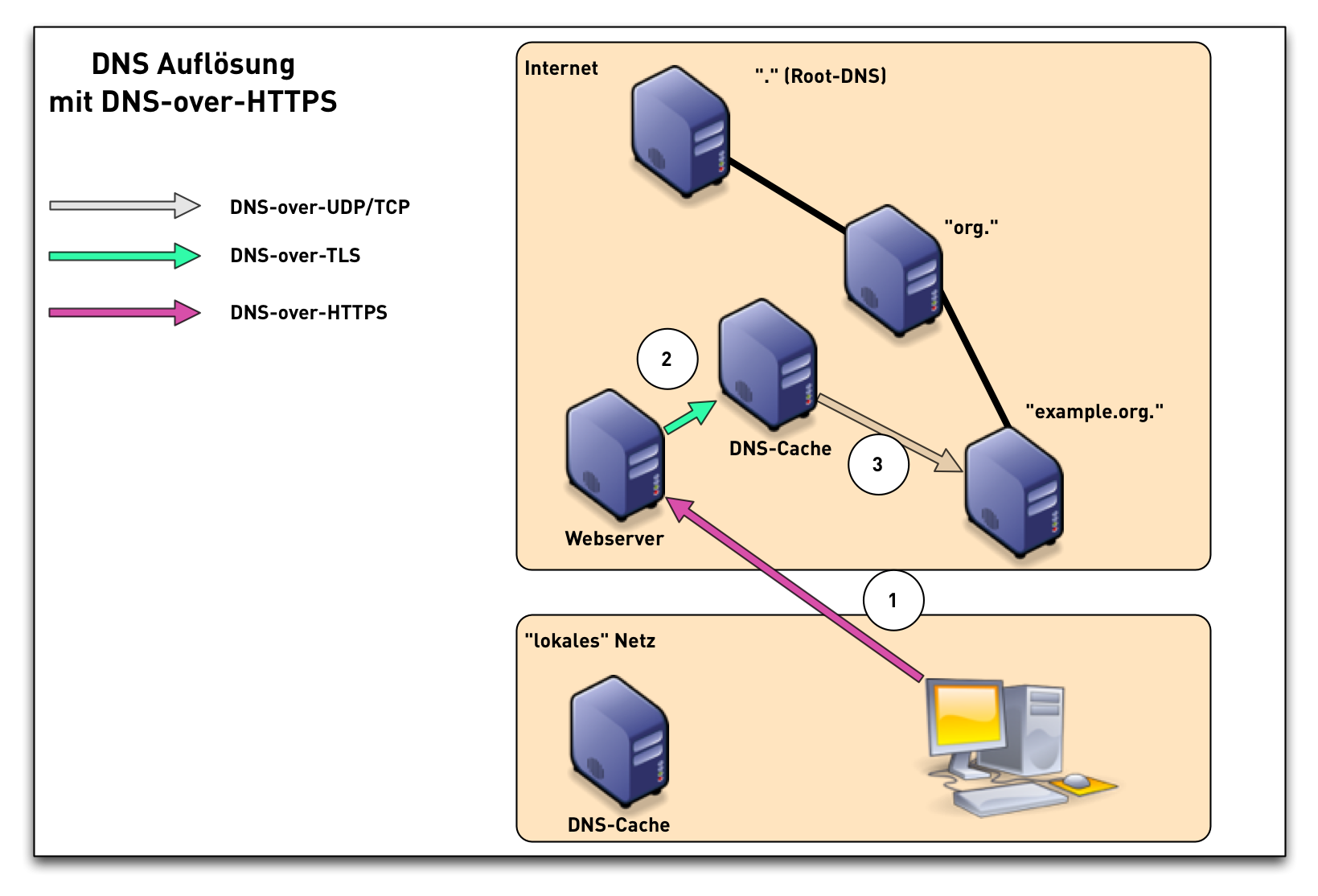
Why?
- HTTPS (Port 443) is already permitted in Firewalls
- easy to use inside (JavaScript) Web-Applications
- most programming languages have HTTP(S) APIs
Developments
- IETF 100 - November 2017 - DNS over HTTP(S) (DoH) working group established: https://datatracker.ietf.org/wg/doh/about/
- IETF 101 - März 2018 - work on DNS Queries over HTTPS finished, start of working group last call (WGLC) in April 2018
- RFC can appear every day now
- Implementations in
C,go,python,rust,javaexist - new implementations pop up every week
DNS-over-HTTPS and IDS/Network-Filter
- Operational Considerations
[…] Filtering or inspection systems that rely on unsecured transport of DNS will not function in a DNS over HTTPS environment.
DoH Client Implementations (1/2)
- Firefox 61+ (disabled by default)
- Firefox TRR Configuration Optionen
URL: about:networking
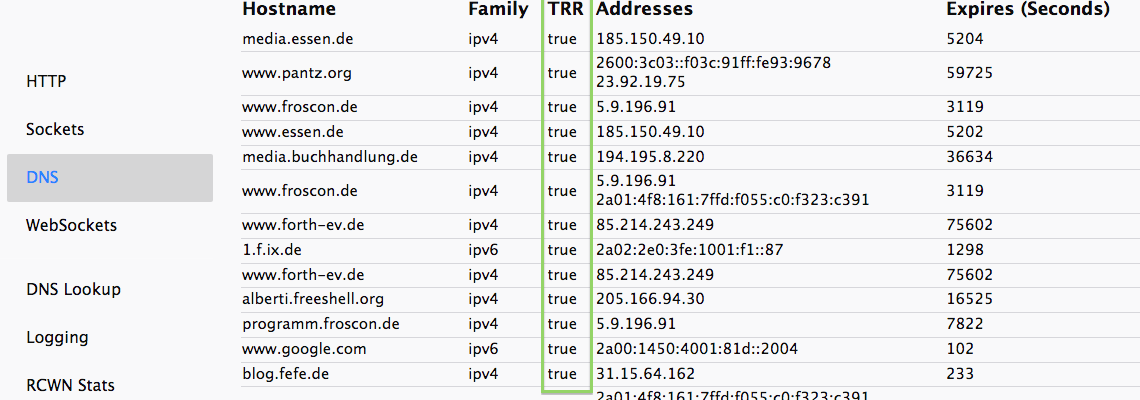
DoH Client Implementations (2/2)
- Bromite Browser "Bromite is Chromium plus ad blocking and privacy enhancements"
cURL(Pull Request on Github)
DoH Resolver/Server
- YourFriendlyDNS
- DNScrypt
- jDNSProxy Simple fast and lightweight DNS proxy and cache, implementing DNS-over-TLS, DNS-over-HTTPS, and Serve-Stale
- m13253/DNS-over-HTTPS High performance DNS over HTTPS client & server
- rust-doh A DNS-over-HTTP server proxy
- doh-proxy A set of python 3 scripts that supports proxying DNS over HTTPS
- dnss a daemon for using DNS over HTTPS (Client + Server)
- DNSCrypt-Proxy implementing DNScrypt and DNS-over-HTTPS
DoH Provider (Selection)
- Cloudflare https://cloudflare-dns.com/dns-query
- Cloudflare/Mozilla https://mozilla.cloudflare-dns.com/dns-query
- Clean Browsing https://doh.cleanbrowsing.org/doh/family-filter/
- PowerDNS https://doh.powerdns.org
- BlahDNS (de) https://doh.de.blahdns.com/dns-query
- SecureDNS https://doh.securedns.eu/dns-query
similar Developments
- RFC 8427 Representation DNS Messages in JSON
- DNS over JSON over HTTPS over TCP
- Google DNS Server-Side https://developers.google.com/speed/public-dns/docs/dns-over-https
- OpenResolve - OpenDNS Server-Side DNS-over-HTTPS Service https://www.openresolve.com/
- dingo - a DNS-Client in Go with Support with Google DNS over HTTPS and OpenResolve https://github.com/pforemski/dingo
- CoreDNS can be used as a DNS-Resolver-Proxy: https://coredns.io/2016/11/26/dns-over-https/
DoQ - DNS over QUIC
- DNS over QUIC over UDP
- Specification of DNS over Dedicated QUIC Connections https://tools.ietf.org/html/draft-huitema-quic-dnsoquic
what is QUIC
- modern TCP-replacement from Google, currently standardized in the IETF
- based on UDP, but implements TCP-like functions
- usually implemented in application, not OS kernels (to fight ossification)
- contains transport encryption similar to TLS 1.3
- 0-RTT
- Performance in par with classic DNS-over-UDP
- QUIC Documents https://tools.ietf.org/wg/quic/
DNS over QUIC
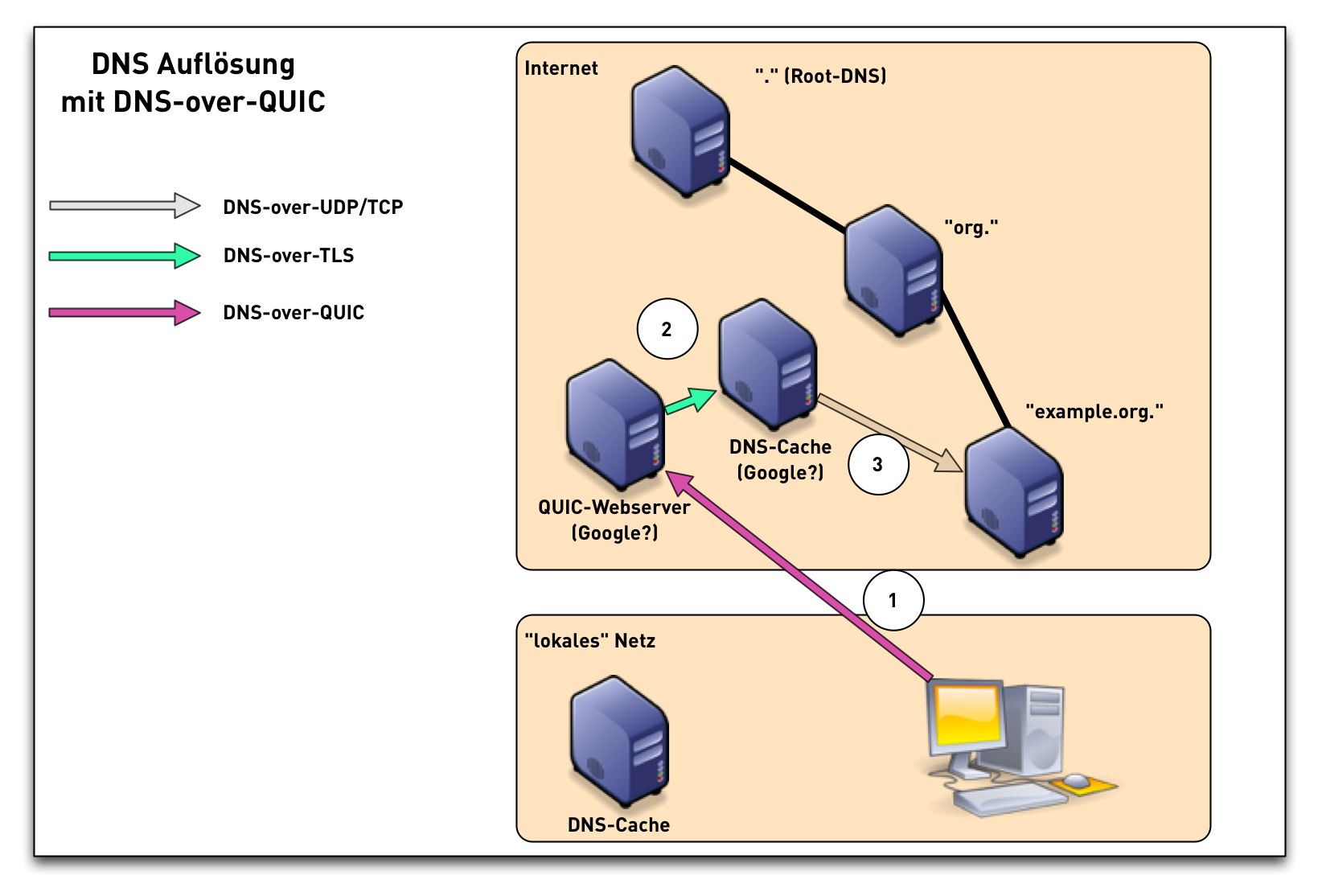
DNS over QUIC comparison
QNAME-Minimization
- classic DNS name resolution has been very chatty
- more data is requested and delivered than needed by modern world DNS
QNAME-Minimization
- RFC 7816 DNS Query Name Minimisation to Improve Privacy
- only DNS-resolver need to be adapted
- DNS-Clients, DNS-Authoritative-Server, Firewalls etc. does not need to change
- QNAME-Minimization is no change in the DNS-Protokolls, only an implementation recommendation
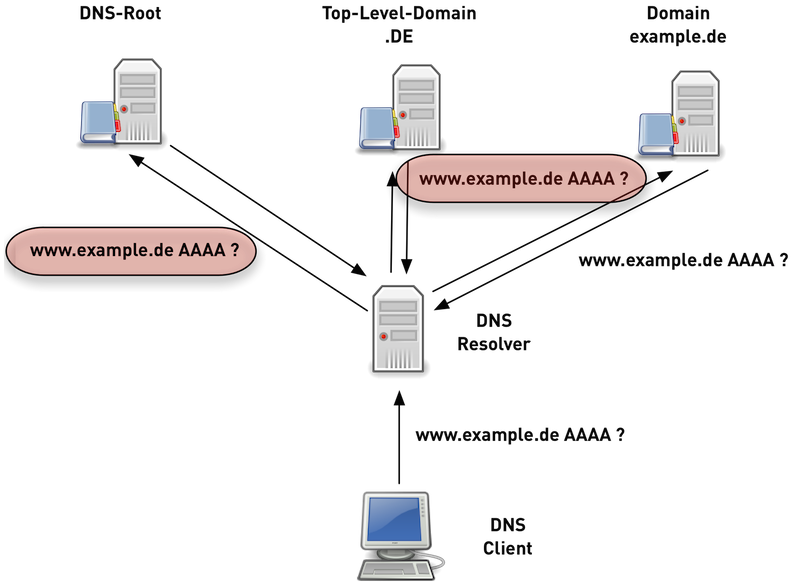
Traditional DNS-Nameresolution (1/6)
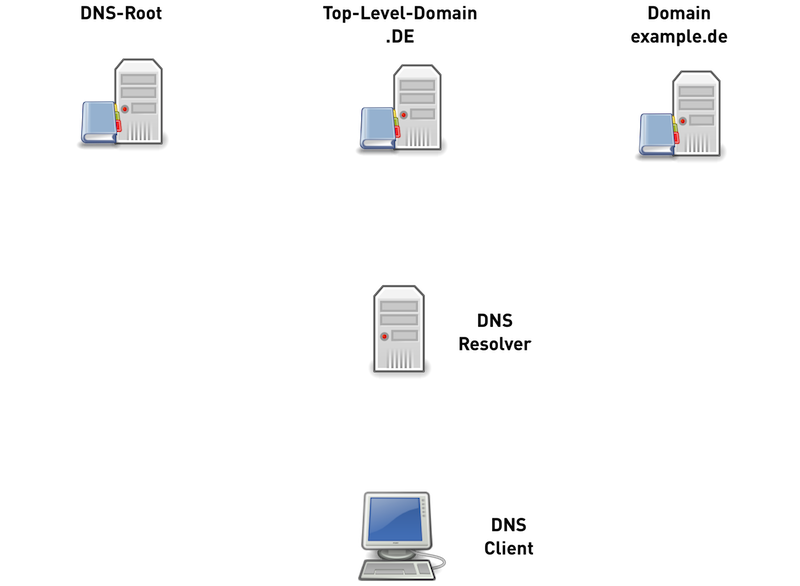
Traditional DNS-Nameresolution (2/6)
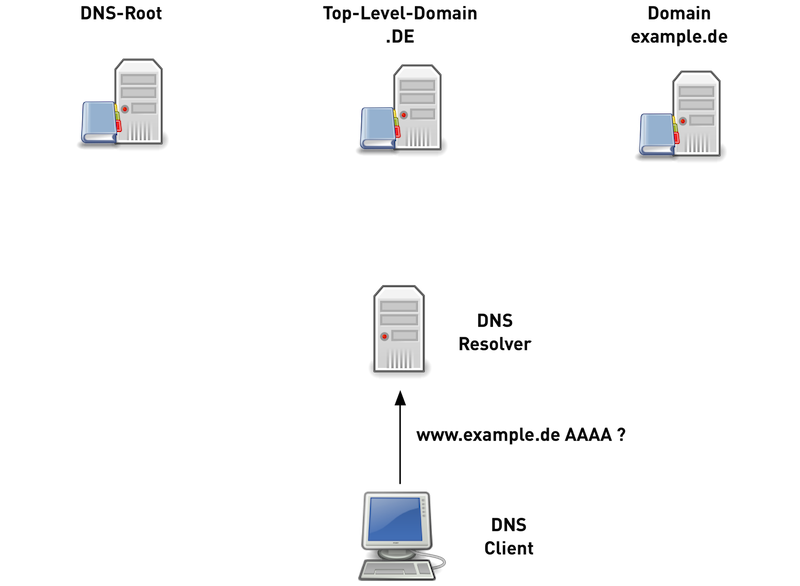
Traditional DNS-Nameresolution (3/6)
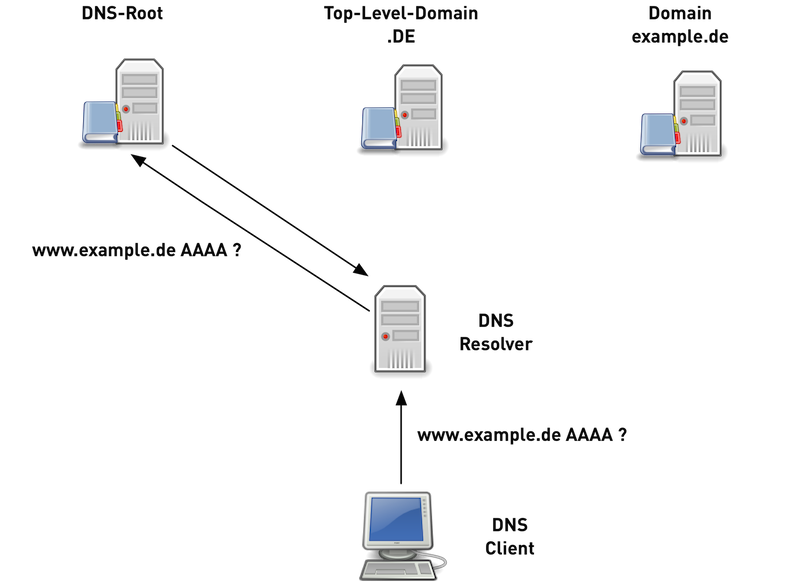
Traditional DNS-Nameresolution (4/6)
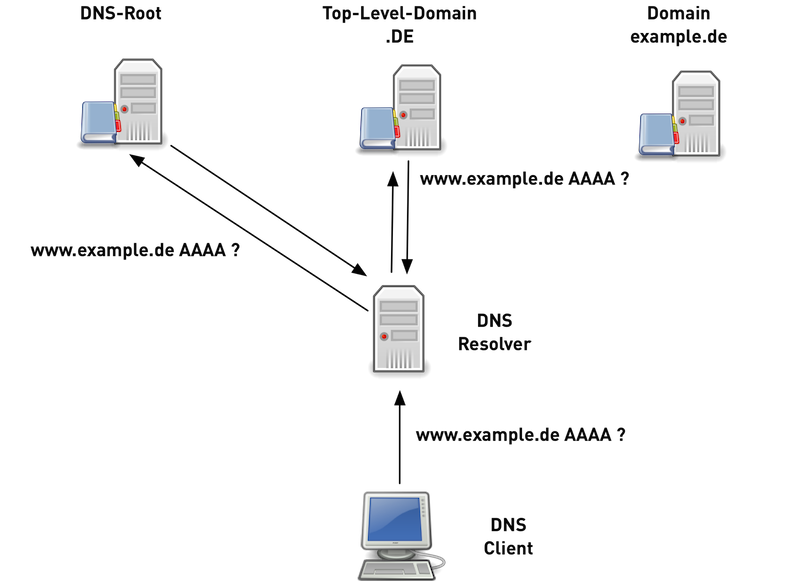
Traditional DNS-Nameresolution (5/6)
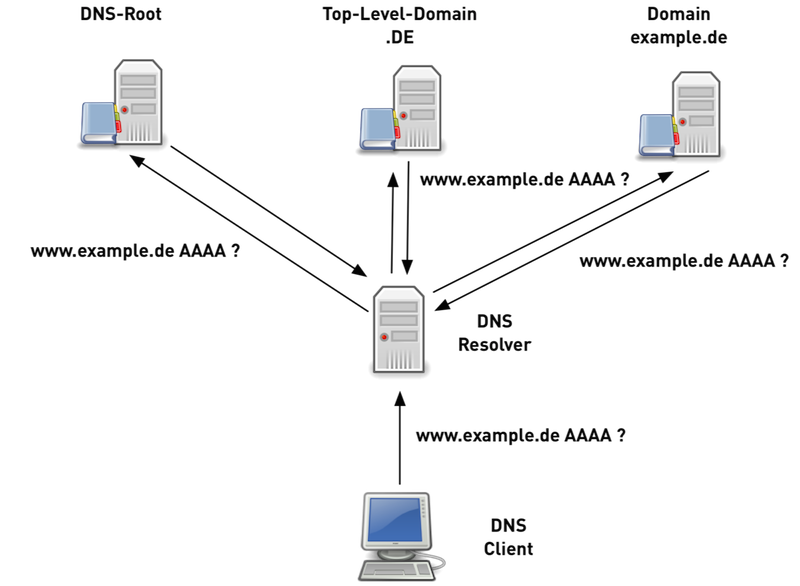
Traditional DNS-Nameresolution (6/6)
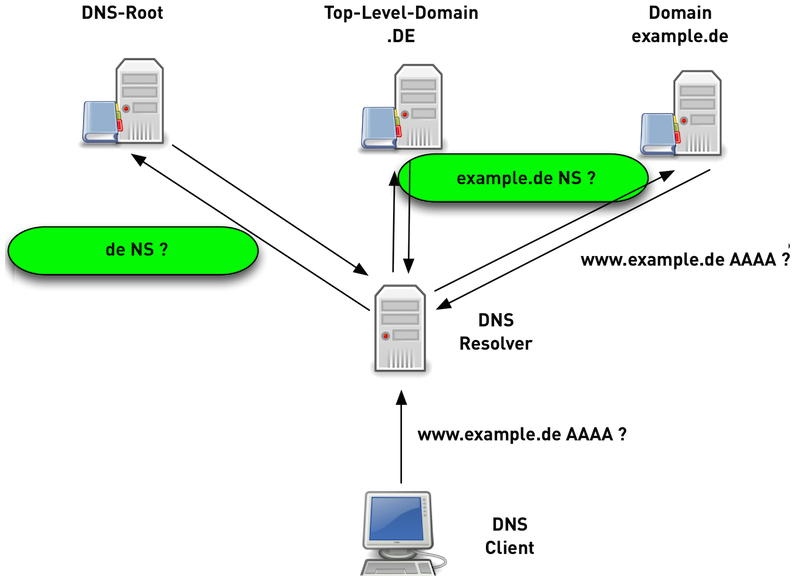
DNS-Nameresolution with QNAME-Minimization
- a DNS-Resolver with QNAME-Minimization knows the structure of DNS delegation in the Internet (Root -> TLD -> SLD …)
- the DNS-Resolver with QNAME-Minimization only requests the bare minimum DNS-Data on on each DNS level
- Performance of DNS-Resolution with QNAME-Minimization is equal to traditional Resolution, and in some cases it is even a little faster.
DNS-Nameresolution with QNAME-Minimization
QNAME-Minimization Implementations
- Unbound
- Knot-Resolver
- BIND 9.13 (in development)
QNAME Minimization test
A simple test from the commandline (using dig) will tell if the
DNS-resolver in use does work with QNAME-Minimization
shell$ dig txt qnamemintest.internet.nl +short a.b.qnamemin-test.internet.nl. "HOORAY - QNAME minimisation is enabled on your resolver :)!"
Summary and looking ahead (1/3)
- the DNS-protocol is evolving fast - maybe too fast (see “The DNS Camel”, or, the rise in DNS complexity and RFC 8324 DNS Privacy, …: Time for Another Look?)
- Communication between DNS-Client and DNS-Resolver will be encrypted in the future (DNS-over-TLS, DNS-over-HTTPS, DNS-over-QUIC)
- DNS-over-HTTPS/QUIC can facilitate centralization, but there is also the potential of de-centralization of DNS-Services
Summary and looking ahead (2/3)
- new DNS-Protocoll Extensions …
- … protect the privacy of users of DNS
- … increase the security of DNS communication
- … decrease the usability of DNS-IDS/Passive-DNS
Summary and looking ahead (3/3)
- what can we do today?
- deploy DNS-over-TLS for the resolver in your network
- (if you know how to operate a service securly in the Internet) deploy a public DNS-over-HTTPS service
- enable QNAME-Minimization in your DNS-resolver (if available)
- monitor your DNS-resolver for malicious traffic
- separate the resolving and authoritative DNS functions
- enable DNSSEC validation
- consider DNSSEC signing your zone
Thank you!
Questions ?
Contact: carsten@menandmice.training or cstrotm@dnsworkshop.de
Thanks to Men & Mice for sponsoring this talk
Presentation created with the help of Emacs 26, Org-Mode and Reveal.js
Don't forget the October 11th KSK-Roll